Icebreaker Pt. 5 – Confidential Homeland Security Undercover Operations Handbook
Washington, DC – As the Trump administration’s immigration policies continue to generate escalating backlash, Immigration and Customs Enforcement (ICE) has come under increasing scrutiny. Journalists, senators, and others attempting to learn more about the agency’s practices have been frequently turned away and/or had their requests denied. ICE is afforded a high level of secrecy by its status as a federal law enforcement agency, operating with virtual impunity and no independent oversight.
While outrage about deportations and human rights abuses by ICE continues to mount, little is known about the day-to-day practices of its agents. In an effort to enable more intimate public knowledge of ICE, and to empower future investigations to ask the right questions, Unicorn Riot is continuing our “Icebreaker” series based on leaked ICE documents obtained by our reporters.
ICE’s rules for informants, infiltration of organizations, and guidelines for breaking the law with protection from federal authorities are all spelled out in an “Undercover Operations Handbook” obtained by Unicorn Riot. The 227 page handbook, which is broken into 14 chapters and 10 appendices, shines light on the secret architecture of America’s informant management operations.
This continues Unicorn Riot’s Icebreaker series of DHS-HSI policy handbook releases. Like the other handbooks, this is also marked OFFICIAL USE ONLY. Future releases will cover other areas of ICE/HSI policy.
#Icebreaker Series - Unicorn Riot series on ICE policy manuals
- Icebreaker Pt 1 – Secret Homeland Security ICE/HSI Manual for Stripping US Citizenship (Feb. 14, 2018)
- Icebreaker Pt 2 – Confidential Homeland Security Asset Forfeiture and Search and Seizure Handbooks (Feb. 22, 2018)
- Icebreaker Pt 3 – Confidential Homeland Security Fugitive and Compliance Enforcement Handbooks (Feb. 28, 2018)
- Icebreaker Pt 4 – Homeland Security Special Agent On-the-Job Training Manual (Apr. 27, 2018)
- Icebreaker Pt 5 – Confidential Homeland Security Undercover Operations Handbook (Jun. 22, 2018)
- Icebreaker Pt 6 – Leaked ICE Special Response Team Handbook for Planning and Executing Armed Raids (Sept. 18, 2019)
- Icebreaker Pt 7 - ICE Case Management Handbook Based on Federal Law Enforcement "System of Systems” (Dec. 13, 2019)
- Icebreaker Pt 8 – Leaked ICE Handbooks for T and U Visa Application Investigations (Dec. 18, 2019)
- Icebreaker Pt 9 – Leaked Interrogation and Arrest ICE Manuals (Jan. 1, 2020)
- Icebreaker Pt 10 – Leaked ICE Agent Private Bill and Commercial Trade Fraud Investigation Handbooks (Jan. 4, 2020)
- Icebreaker Pt 11 – Bush/Clinton Era Customs Investigators Manuals (Feb. 13, 2020)
A FOIA by GovernmentAttic.org established that this 2008 manual has been in effect for at least 8 years – from April 2008 to the end of 2016. Current versions of the handbook are believed to be highly similar to this edition, with some new materials likely added over the last two years.
ICE employees are directed to conceal the “Undercover Operations Handbook” from discovery by defense attorneys for clients prosecuted as a result of DHS activities. The handbook contains the agency’s guidelines for infiltrating religious, political and media organizations, as well as how to pay off informants using stipends and/or commissions. Also included is information on undercover training school programs, and details about how ICE conducts undercover activity outside the United States and on the Internet. The manual also states that officers from “another federal, state, or local law enforcement agency” may voluntarily work undercover in operations directed by ICE.
The handbook is packed with arcane details of federal investigations. Also contained in the text is the command structure for ICE agents to obtain approval to break federal laws, as well as policies for creating false identities and inserting falsified records into government databases.
The “Undercover Operations Handbook” describes how to recycle profits from potentially illegal undercover operations into secret budgets where money can be used to fund ICE operations, pay overtime costs for DHS agents, funnel cash to informants, and make payouts to other agencies and foreign governments. Also revealed in the handbook is the existence of ICE “undercover contract psychologist” staff tasked with mitigating psychic trauma suffered by ICE operatives and informants, keeping personnel in action if possible.
The manual specifies numerous policy details that agents are supposed to follow. When running shell companies to conceal fake businesses (what ICE calls “proprietaries”), operatives are reminded that associated bank balances should be kept under $100,000 due to insurance limits. When creating “backstopped” fake identities for ICE shell companies, various corporate property, finance and aircraft registration systems are used to create cover. According to the manual, the business information company Dun & Bradstreet can provide fake commercial reports to help conceal undercover ICE operations.
A note in the manual cautions the reader that “advances in technology have eroded the ability of law enforcement” to maintain fake identities and shell companies created to hide undercover operations. ICE agents are encouraged to “understand the limits of their backstopping and to have contingency plans in place for situations when investigative targets question alias information.”
The role of informants in ICE operations doesn’t get a lot of press. ICE informant policies got attention around the “House of Death” case, where ICE informant Guillermo Ramirez Peyro was believed to have murdered David Castro. (The website NarcoNews covered this case and obtained related ICE internal materials including a 2003 interim ICE Undercover operations manual.)
One seasoned observer pointed out to Unicorn Riot that a key dimension to consider in a policy manual like this is how the handlers keep the informants working for them. The handbook goes into exhaustive detail about how informants can be financially compensated and allowed by ICE to commit profitable crimes. Chapter 11 of the manual covers ICE’s use of psychologists to keep informants operating in potentially traumatic situations.
Diving into the Undercover Operations Handbook
- The complete 227-page manual is available here for download (PDF – 989KB).
- Download a pack of more than 80 screencaps from the document to share and research further: icebreaker5-images-final (ZIP – 14.5MB).
The entire handbook is embedded below:
ice-undercover-operationsTo make the most sense of this material, the glossary in Appendix G (p198) is a good place to begin. The index in Appendix H (p214) shows where these terms lie throughout the manual. Key points from the handbook chapters will be summarized below, and glossaries below that. (All pages here refer to the page of the PDF itself, not the number printed on the footer of the pages.)
We need your help: If you’re on social media, you can share the hashtag #ICEBREAKER with the page number you found something interesting, or email [email protected] with Icebreaker in the subject line.
- Chapter 1 PURPOSE AND SCOPE
- Chapter 2 BACKGROUND AND AUTHORITY
- Chapter 3 LEGAL/LIABILITY ISSUES
- Chapter 4 ROLES AND RESPONSIBILITIES
- Chapter 5 UNDERCOVER OPERATION APPLICATION AND APPROVAL PROCESS
- Chapter 6 ADMINISTRATIVE AND FINANCIAL MANAGEMENT OF UNDERCOVER OPERATIONS
- Chapter 7 MANAGEMENT CONTROLS AND REPORTING REQUIREMENTS FOR UNDERCOVER OPERATIONS
- Chapter 8 TRAINING
- Chapter 9 UNDERCOVER IDENTIFICATION AND BACKSTOPPING
- Chapter 10 UNDERCOVER LIAISON COORDINATOR PROGRAM
- Chapter 11 TRAUMATIC INCIDENT RESPONSE (PSYCHOLOGICAL SERVICES)
- Chapter 12 UNDERCOVER ACTIVITY IN FOREIGN COUNTRIES
- Chapter 13 UNDERCOVER INTERNET ACTIVITY
- Chapter 14 PROCEDURES FOR CLOSING CERTIFIED UNDERCOVER OPERATIONS
- Appendix A Authorities
- Appendix B CUFFS Expense/Advance Approval Form
- Appendix C Pick-Up Log for Undercover Operation
- Appendix D Property/Equipment Log for Undercover Operations
- Appendix E Undercover Operation Monthly Financial Review Worksheet
- Appendix F Table of Transgressions and Corrective Actions
- Appendix G Glossary
- Appendix H Index
- Appendix I Superseded Documents
- Appendix J Acronyms
CHAPTER 1: PURPOSE AND SCOPE
“The Undercover Operations Handbook provides a single source of national policies, procedures, responsibilities, guidelines, and controls for U.S. Immigration and Customs Enforcement (ICE), Office of Investigations (OI) personnel when conducting undercover activities, investigations, and operations.”
“If disclosure of this Handbook or any portion of it is demanded in any judicial or administrative proceeding, the OI [Office of Investigations] Information Disclosure Unit, Mission Support Division (MSD), as well as the appropriate ICE Counsel and/or U.S. Attorney shall be consulted so that appropriate measures can be taken to invoke privileges against disclosure. This Handbook contains information which may be exempt from disclosure to the public.”
(Note that “OI” or Office of Investigations is the predecessor to the Homeland Security Investigations unit of ICE, which expanded and rebranded itself as the Department of Homeland Security has grown larger and more well-funded.)
CHAPTER 2: BACKGROUND AND AUTHORITY
Chapter 2 includes objectives of undercover activities, which can be as vague as trying to “gather intelligence that allows management to evaluate threats, reallocate resources, and organize enforcement activity.”
Brief recaps of DHS Sensitive Circumstances, ICE Sensitive Circumstances.
CHAPTER 3: LEGAL/LIABILITY ISSUES
This 22-page section covers the detailed world of “Otherwise Illegal Activity” permitted for informants authorized to commit crimes. Includes entrapment, inducements to engage in criminal activity, the search authority of undercover operatives, altering vehicles, working with third parties, the Personal Assistance Agreements, and maintaining covertness with insurance claims.

p18: Otherwise illegal activity includes trafficking in immigrants, buying stolen goods, drug trafficking and paying bribes.
p19-20: A lot of opportunities to induce people to engage in criminal activity are available, including the low bar of a “reasonable expectation that offering the inducement will produce evidence of other illegal activities.”
Criminal activities resulting in violence and entrapment issues are also highlighted:

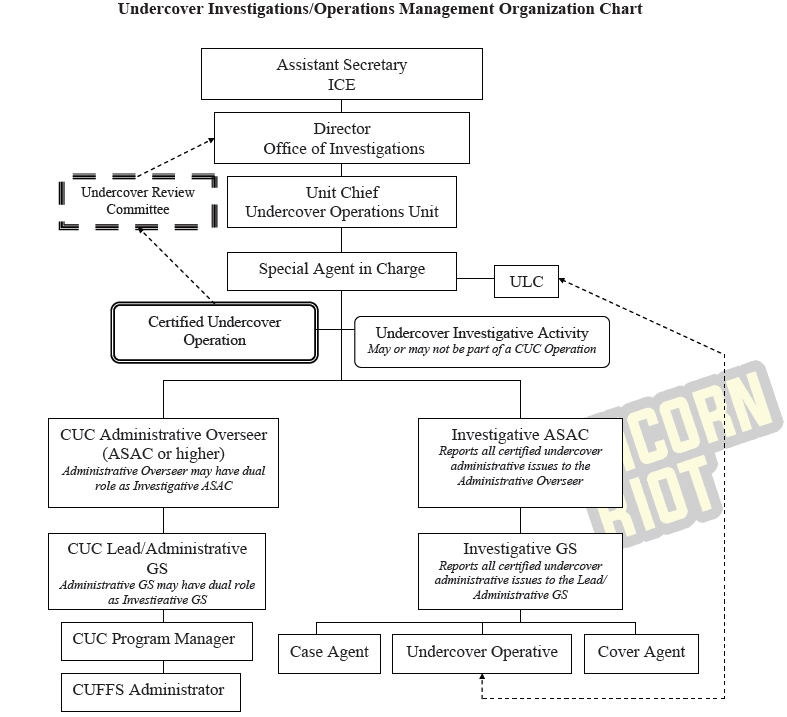
CHAPTER 4: ROLES AND RESPONSIBILITIES
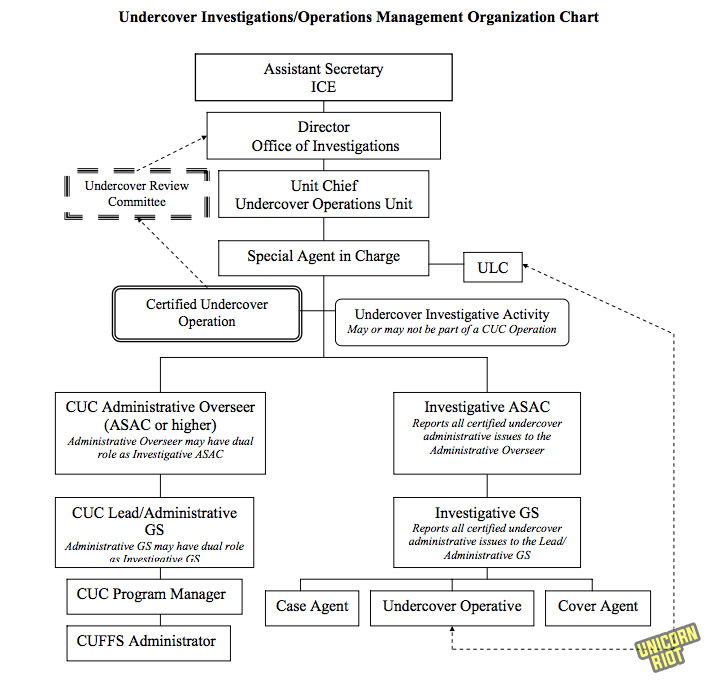
This 22 page chapter covers the many job titles involved with authorizing and managing covert operations and illegal activities.
The Undercover Review Committee (URC) is a critical oversight body. The Undercover Liason Coordinators play a critical role in stitching the operations together.
The Unit Chiefs in several sections including Undercover Operations Unit, ISD, Investigative Programs and Operations manage other activities.
Cover agents, case agents, contact agents and ‘Certified Undercover Fundamental Financial System’ (CUFFS) administrators handle the informants and their cashflows the most closely.
The manual warns that the CUFFS Administrator position is sensitive to “stress-related problems or career stagnation” and that personnel should be rotated accordingly.
CHAPTER 5: UNDERCOVER OPERATION APPLICATION AND APPROVAL PROCESS
This 22 page chapter covers every level of detail for initiating covert operations and planning them. Sensitive circumstances for special oversight including media, religious and political infiltration are included, which triggers review from the Undercover Review Committee (URC).
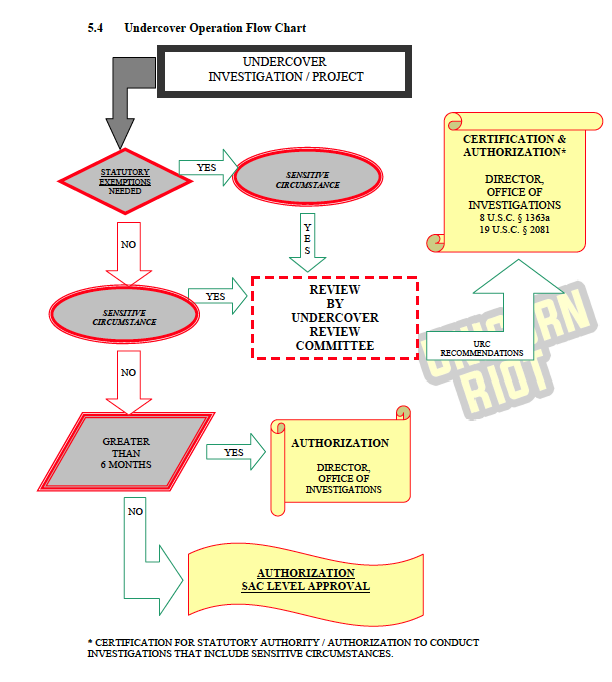
p53: A flowchart indicates the flows of authority and operations patterns. If sensitive conditions are not triggered then the Director, Office of Investigations approves it if it runs longer than 6 months. If not, it is authorized on the Special Agent in Charge (field office leader) level.
p60-63: It includes coordination with the Department of Justice and DEA.
p63-68: Sections that cover when operations go awry cover emergency exigent approval, emergency approval and unforseen circumstances.
CHAPTER 6: ADMINISTRATIVE AND FINANCIAL MANAGEMENT OF UNDERCOVER OPERATIONS
This 46 page chapter covers how funds are managed in ongoing undercover operations mainly using a Quickbooks-based system called CUFFS to record many activities. This is by far the most detailed information about CUFFS to surface in public.
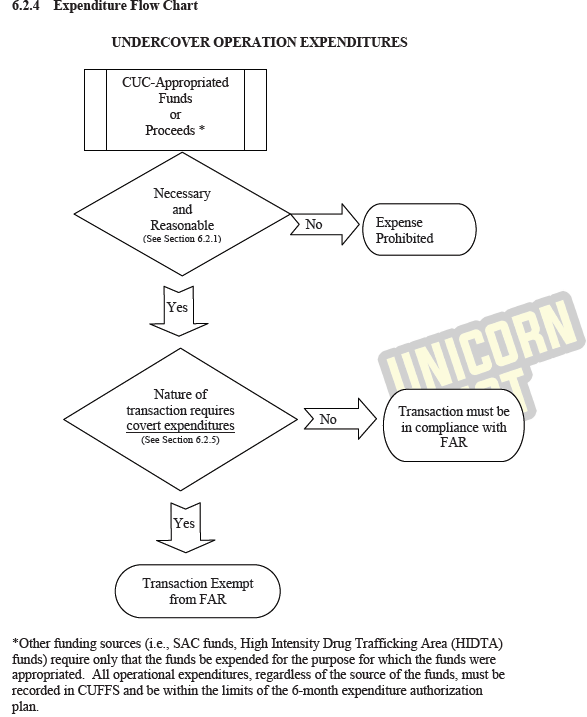
p72: Expenditure flowcharts are included. High Intensity Drug Trafficking Area (HIDTA) programs can also provide funding.
“Proceeds” are the profits from sometimes illegal proprietary or undercover businesses operated by informants or agents. Proceeds can in turn provide a cash flow for lots of activity.
Proceeds can be split with other undercover operations during a joint operation. It can also be split with other agencies through a Memorandum of Agreement, or even with foreign law enforcement agencies.
Information and evidence can also be purchased with proceeds, and overtime can also be paid out from proceeds. Thus an ongoing secretly government controlled operation which might be illegal (for example money laundering) can put money into a number of pockets on an ongoing basis, be it other agencies, ICE agents’ overtime or underworld figures.

It discusses undercover operations going longer than a year and how to use proceeds for travel expenses in that context. Proceeds should always be kept below $500,000 if possible.
CHAPTER 7: MANAGEMENT CONTROLS AND REPORTING REQUIREMENTS FOR UNDERCOVER OPERATIONS
This 11 page chapter covers certain oversight mechanisms. The National Program Managers and on-site field reviews are critical components. The TECS system is used for case management, and includes the Primary Case File and property inventories.
It also includes managing transgressions within certified undercover operations, covered in great detail in Appendix F.
CHAPTER 8: TRAINING

This three page chapter covers several different ICE schools: The Undercover Operatives School, the Undercover Managers School, the Undercover Liaison Coordinator School, the CUFFS Administrator School, and training the Undercover Operations Unit Jump Team.
CHAPTER 9: UNDERCOVER IDENTIFICATION AND BACKSTOPPING
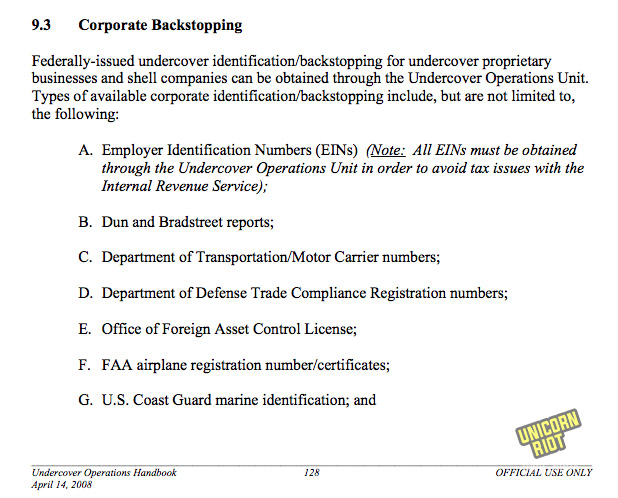
This nine page chapter covers how ICE/HSI can fabricate identities of people and businesses in a “backstopping” process. This includes fake IDs from federal, state, foreign governments and private businesses.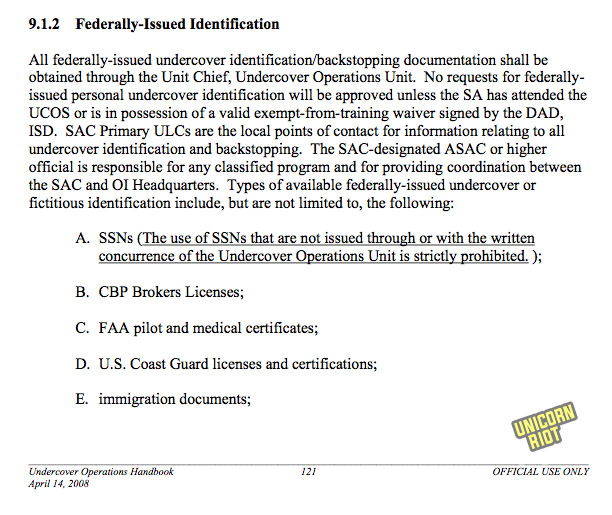
It also includes fake financial histories, individual bank accounts and credit cards, and using multiple undercover businesses.

CHAPTER 10: UNDERCOVER LIAISON COORDINATOR PROGRAM
This five page chapter covers how undercover liaisons help design the undercover operations including a recommended battery of psychological evaluations of informants.

CHAPTER 11: TRAUMATIC INCIDENT RESPONSE (PSYCHOLOGICAL SERVICES)
This two page chapter covers how psychologists and the ICE Employee Assistance Program mitigate the psychological trauma on ICE agents for working on undercover operations.
CHAPTER 12: UNDERCOVER ACTIVITY IN FOREIGN COUNTRIES
This one page chapter covers logging undercover activities in foreign locations.
CHAPTER 13: UNDERCOVER INTERNET ACTIVITY
This two page chapter covers limited and certified investigative activities and electronic recordkeeping.
CHAPTER 14: PROCEDURES FOR CLOSING CERTIFIED UNDERCOVER OPERATIONS
This eight page chapter covers liquidating assets and disposing property of covert operations, as well as closing the CUFFS finance tracking files.
Finally we move to the appendices which are extensive and form more than a third of the content of the handbook.
APPENDIX A: Authorities
This four page section covers the areas of US Code related to the authorities claimed in the manual.
APPENDIX B: Certified Undercover Operation CUFFS Expense/Advance Approval Form
The form to fill in for many types of undercover transactions, for later entry by the CUFFS-assigned officer into Quickbooks.
APPENDIX C: Pick-Up Log for Undercover Operations
Form to fill in on pickups like cash or Electronic Fund Transfers (ETFs) during undercover operations. Includes “points” which may be money laundering percentages.
APPENDIX D: Property/Equipment Log for Undercover Operations
The log for acquisitions including the locations.
APPENDIX E: CERTIFIED UNDERCOVER OPERATION MONTHLY FINANCIAL REVIEW WORKSHEET
An instructional sheet on data input, with a worksheet for monthly financial review. Includes areas for comment if bank balances are above $100,000, as well as any outstanding liabilities.
Includes undeposited funds and bank reconciliation forms. Income and expenses by all classes should be reported. It includes the following warning:
“The Undercover Operations Handbook contains guidance for necessary and reasonable expenditures. Look for unusual transactions or spikes in expenses. For example, you have seen approved monthly cell phone expenses totaling $200- $300 in previous months. This month, you find that the same cell phone expenses are $4,000. Ensure that operational funds are not supplementing non-operational expenses (general SAC office budget). The same applies to other expenses, advances, vehicles, etc.”
Forms for expenditure approval levels and property are also included.
Third party payments, stipends and commissions should be logged using ICE 73-293 forms.
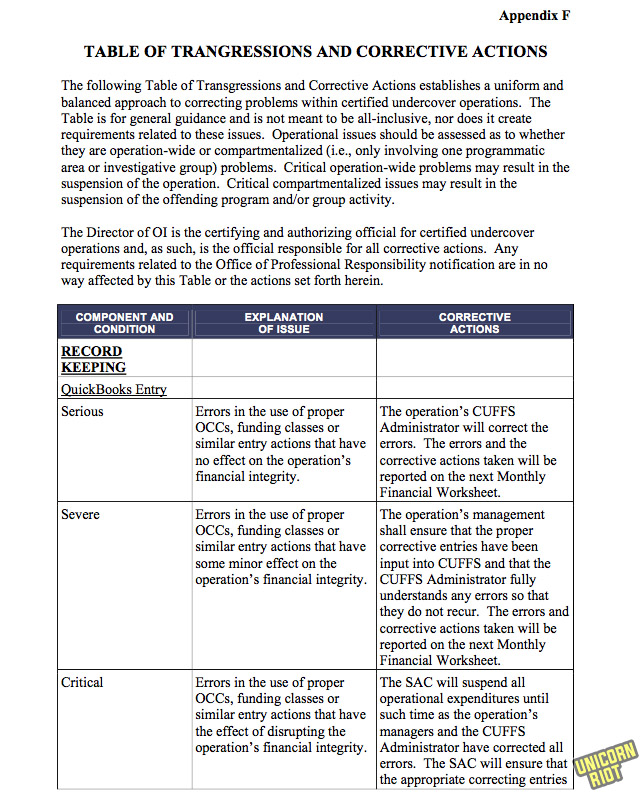
APPENDIX F: TABLE OF TRANSGRESSIONS AND CORRECTIVE ACTIONS
This twelve-page chart shows “general guidance” for different types of “transgressions” like mistakes, sloppy bookkeeping and potential corruption in managing undercover operations.
APPENDIX G: GLOSSARY
p199: Business/Purchase Exemption: the loopholes for front companies or “proprietary businesses” to circumvent the usual rules for government-owned corporations.
Certified Undercover Fundamental Financial System (CUFFS): The overall financial recordkeeping for “undercover operations”. A huge section of the manual addresses proper recordkeeping in CUFFS — and what happens when people break the rules in lots of subtle ways.
Commissions: financial compensations for informants, investigations targets, and profits from criminal activities.
p200: Confidential informant: working under the direction and control of a federal law enforcement representative. (aka Cooperating Individual)
Credit/Debit Card: includes cards issued on fictitious personal or corporate names “to strengthen an undercover activity”
p201: Entrapment: a defense to a criminal charge on the theory that Government agents cannot “originate a criminal design, implant in an innocent person’s mind the disposition to commit a criminal act, and then induce commission of the crime so that the Government may prosecute.” The two elements are government inducement of the crime and the defendants lack of predisposition to engage in the criminal conduct, which is ‘by far the more important’.
Joint Undercover Operations: includes multiple law enforcement agencies and can include splitting the proceeds.
p202: Money Laundering Points: percentages paid to or from a target, or fees for money laundering.
Nexus to Undercover Activities: “A direct link to an open undercover investigation and the undercover activity of that investigation. All investigations placed under a certified undercover operation MUST have undercover activity or a direct nexus to the operation’s undercover activity.” [Emphasis in original]
p203: Otherwise Illegal Activity (OIA): A central concept in this manual is the idea that some things aren’t illegal if they are authorized; it’s defined here in a negative sense: “Except when authorized pursuant to ICE policy and this Handbook, no undercover operative will participate in any activity that would constitute a crime under federal, state or local law if engaged in by a private person acting without authorization.”
Personal Assistance Agreement (PAA): Agreement between a confidential informant / cooperating individual and Special Agent in Charge (SAC) that details activities, responsibilities and limitations. This can also state the amounts including commissions and compensation they can expect to receive. PAAs require approval of Unit Chief, Investigative Support Unit (ISU).

Proceeds

Proprietary Undercover Business

Sensitive Circumstances Related to Undercover Activity: DHS and ICE: This four-page extended description covers some of the most politically impactful undercover operations ICE might undertake, including spying on politicians, nominees for government agencies, foreign officials, religious or political organizations or the news media interfering with government activity, running businesses that deal directly with the public, transporting “illegal aliens across an international border” and running “stash house” operations, and some illegal activities. Also includes marriage stings, and providing perjurious and false information to courts and administrative proceedings. This could even include giving testimony while undercover in the false persona.
DHS sensitive circumstances also could involve jumping into meetings with people and lawyers, or even acting as a lawyer while undercover. An undercover operative could be an attorney, physician, psychologist, clergy, spouse, news media or other role with legal confidentiality obligations.


ICE has its own set of additional sensitive circumstances, including hazardous materials, operations that run longer than a year, third-party funding from outside the government, running businesses not reachable by the general public, off-site locations, using the proceeds of a undercover operation to pay off expenses, and if a bank account is operated.
Undercover Activity: includes several classes like internet-based, limited, moderate and deep undercover activity.

Undercover Review Committee: there are two URC groups: DHS and ICE URC’s.

APPENDIX H: INDEX
Key term index of the whole manual and terms that are used throughout – in outlining (rather than page number) format. A quick scan here will give the reader a good view of all the key terms.

APPENDIX I: SUPERSEDED DOCUMENTS
A list of various directives and memoranda that made up the informant policies since ICE was created in 2003.
APPENDIX J: ACRONYMS
Three pages of acronyms complete this long policy handbook.
Unicorn Riot will continue the Icebreaker series in the months to come, with more policy handbooks provided in full.
Please consider a tax-deductible donation to help sustain our horizontally-organized, non-profit media organization:

#Icebreaker Series - Unicorn Riot series on ICE policy manuals
- Icebreaker Pt 1 – Secret Homeland Security ICE/HSI Manual for Stripping US Citizenship (Feb. 14, 2018)
- Icebreaker Pt 2 – Confidential Homeland Security Asset Forfeiture and Search and Seizure Handbooks (Feb. 22, 2018)
- Icebreaker Pt 3 – Confidential Homeland Security Fugitive and Compliance Enforcement Handbooks (Feb. 28, 2018)
- Icebreaker Pt 4 – Homeland Security Special Agent On-the-Job Training Manual (Apr. 27, 2018)
- Icebreaker Pt 5 – Confidential Homeland Security Undercover Operations Handbook (Jun. 22, 2018)
- Icebreaker Pt 6 – Leaked ICE Special Response Team Handbook for Planning and Executing Armed Raids (Sept. 18, 2019)
- Icebreaker Pt 7 - ICE Case Management Handbook Based on Federal Law Enforcement "System of Systems” (Dec. 13, 2019)
- Icebreaker Pt 8 – Leaked ICE Handbooks for T and U Visa Application Investigations (Dec. 18, 2019)
- Icebreaker Pt 9 – Leaked Interrogation and Arrest ICE Manuals (Jan. 1, 2020)
- Icebreaker Pt 10 – Leaked ICE Agent Private Bill and Commercial Trade Fraud Investigation Handbooks (Jan. 4, 2020)
- Icebreaker Pt 11 – Bush/Clinton Era Customs Investigators Manuals (Feb. 13, 2020)