Oracle, Chat & Raw Code Found in Mossack Fonseca Offshore Web Portal
Unicorn Riot can report that the Panama-based offshore specialist law firm Mossack Fonseca has set up its customer portal with very incorrect server settings, inadvertently publishing much of its source code to the public with no barriers to casual browsers. We can state with certainty that Mossack Fonseca has a customer “portfolio” portal that can set up chats & also use Oracle “middleware” to host customer portal activity, in order to help billions of dollars evade government tax authorities around the world.
Among recent #PanamaPapers stories, on Tuesday, April 5th, Forbes.com staff writer Thomas Fox-Brewster reported that Mossack Fonseca’s customer service portal was running a old version of Drupal that has at least 25 security vulnerabilities (details here). Further investigation by Unicorn Riot of openly available data on this portal, requiring no authentication whatsoever, revealed the bulk of the back-end structure of the Drupal portal.
Unicorn Riot has discovered that Mossack Fonseca ran Oracle’s HTTP Server middleware product, which is a fork of the widely used open source program Apache 2.2; it is so badly misconfigured that it publishes for any visitor much of the inner code of the customer portal as raw text. This serious misconfiguration of the Oracle HTTP server is entirely separate from known (& long since patched) Drupal vulnerabilities and no Drupal-based vulnerabilities were exploited to view this published data.
Mossack Fonseca publishes its own portal’s file structure…
The public changelog indicates Drupal 7.23 is likely the active version. The first public attention called to this URL was in a tweet by this author, who was soon cited as correct by well-known Finnish security specialist Mikko Hypponen.
Forbes is probably right https://t.co/g4mkPd5fyJ Mossack Fonseca didn’t update their #Drupal see > https://t.co/ADtvq9JXX4 priceless! Epic
— Dan Feidt~hongpong (@HongPong) April 5, 2016
A few hours later, Wired Magazine’s UK affiliate published an article, following up on Forbes’ previous article about Mossack Fonseca’s many security vulnerabilities, this time including the Changelog URL (without attribution!). As Wired UK vaguely pointed out, the Changelog – a simple text file – is hardly the only file which the portal serves up without challenge to any visitor. A writeup on Drupal.ovh extended this tweet’s idea to consider if the old Drupal code contributed to the PanamaPapers leak.
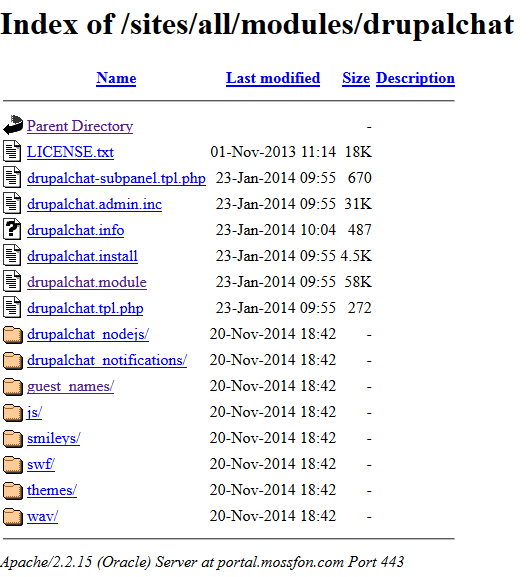
When examining the materials Mossack Fonseca published inside https://portal.mossfon.com/sites it is obvious that the “indexes” listing function, a feature of Apache and thus Oracle HTTP server, is turned on. On a correctly configured Apache server, the .htaccess file placed in the root directory will prevent all of these effects if permission is set correctly on the server. Currently, it lists all the files in the directory, and linked child directories also have contents listed accordingly.
Traversing this published set of URLs in any browser, much as a search engine automatically would, leads then to portal.mossfon.com/sites/default which hosts the settings.php file that contains the master database connection strings for a normal site. Fortunately for Mossack Fonseca, files ending in .php are not “printed out” in full text when requested. However, in another sign .htaccess is not working, it appears PHP files are executed in an immediate context, appearing when attempting to verify if they were simply published. (This means that if someone could manage to upload a malicious PHP file they would be able to run it simply by requesting the URL of the uploaded file, another huge vulnerability.)
The folder at portal.mossfon.com/sites/default/files (at the standard location for Drupal 7 uploads) only seems to contain tacky clip art associated with the theme of the site, and sadly, not the multiple terabytes of shell company documents making worldwide headlines.
Other URLs that typically respond on Drupal sites such as portal.mossfon.com/user/1 , which on many sites would show the name of the root administrative account, return Oracle HTTP server 404 errors (and not Drupal-generated 404s). This is another clue that Oracle is causing some shift away from Drupal’s default behavior in Apache.
… and most of the PHP source code is published too!
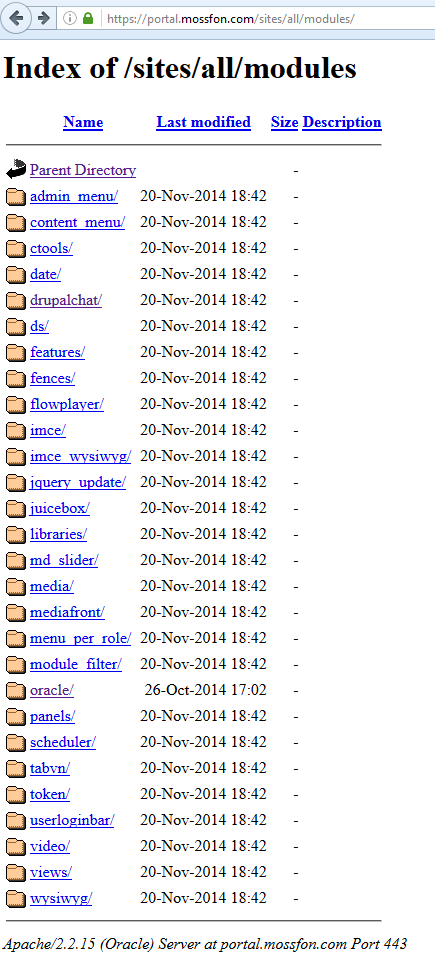 The most striking component inadvertently published by Mossack Fonseca is within portal.mossfon.com/sites/all/modules which shows the list of all the non-core modules added to the site by its developer. A folder there called “oracle” is an official module that allows Drupal to use Oracle databases directly.
The most striking component inadvertently published by Mossack Fonseca is within portal.mossfon.com/sites/all/modules which shows the list of all the non-core modules added to the site by its developer. A folder there called “oracle” is an official module that allows Drupal to use Oracle databases directly.
Surprisingly, all the files ending in .module are published by Mossack Fonseca in plain text for anyone to see. In Drupal parlance, the core code of the modules that compose the entire system, including add-ons, are stored in files with a .module suffix.
The community Oracle module has not been updated since 2013, similar to the vintage of much of the site (November 2014 seems to be the last time the site was generally worked on with some exceptions. It changed in mid-2015 at portal.mossfon.com/modules – mostly but not entirely core modules ).
“Drupalchat” could setup local chat windows
The “drupalchat” module is also installed, which can start browser-based conversations, including using local nodejs backends.
Web servers use file suffixes to decide what to do during visitor requests for URLs. .JPG files, for example, are served with headers to warn the browser an image is coming. Because of apparent incompetence, the feature that is supposed to refuse to publish .module file text has not been activated, and instead the module code is always published as plain text. (However, PHP “includes” with the suffix of “.inc” are correctly forbidden)
Mossack Fonseca’s offshore company customer service empire is Oracle powered, and not security patched
The presence of Oracle as a database provider and HTTP server provider is an important indicator of how Mossack Fonseca designed its digital business processes, and a potent clue about how the data may have leaked out. Using the expensive Oracle platform as a database for their portal – instead of the widely used MySQL (which Oracle acquired as part of Sun Microsystems in 2010), or its free software replacement MariaDB – would most likely be one element in a larger business platform.
This design – Oracle ‘middleware’ & backend with a Drupal portal front-end, would let customers remotely view and download a folder of file attachments including legal documents for shell companies. Generally, it would not make business sense to simply get expensive Oracle database & Oracle HTTP server middleware just to run a site in isolation from a larger set of data.
Since they apparently abandoned doing any Drupal security updates for at least the last two years, they did not wisely use the proceeds from setting up hundreds of thousands of shell companies to secure their digital platform in industry-standard ways. These problems are not PhD-level computer science vulnerabilities, but simple configuration and maintenance than any second-year CS student could probably perform adequately. Automated Drupal tools are available which would have alerted Mossack Fonseca to these problems.
Clue to Panama Papers possible hack? Mossack Fonseca published custom Drupal code showing online “portfolio” viewing system
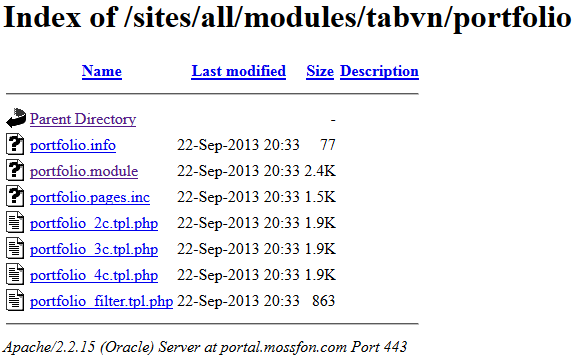
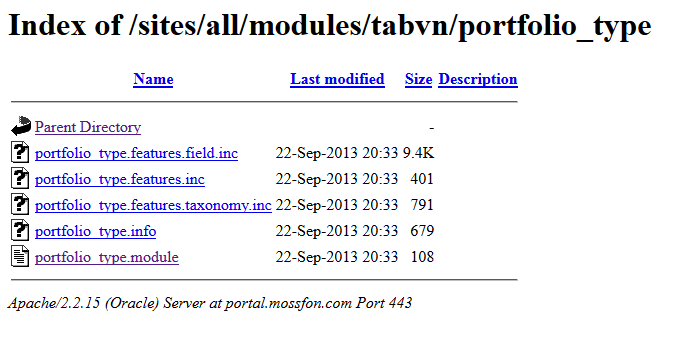
A set of custom code is also in /sites/all/modules/tabvn, composed of several modules. While much of the code is in unpublished “.inc” files, Mossack Fonseca published enough code to indicate that a Drupal display was coded to show something called “portfolio” content. This code is a good example of what a developer would call “glue code” to provide a customized display.
This leads to a very likely conclusion that the portal was not just used for more limited tasks like making sure one’s customer contact information was up to date. Instead, this “portfolio” function could potentially access files stored in a larger Oracle database.
This Drupal instance is known to be insecure. Its version is older than the exposure of Drupal’s worst lifetime security flaw. (WordPress shared a similar flaw & both were patched in a harrowing day; October 15, 2014 is remembered as “Drupalgeddon”).
By exploiting the Drupalgeddon flaw it could have been possible for a skilled intruder to make off with important site access data, and subsequently could pose as any user or the root administrator.
For example, a ‘session hijacking’ attack could have leveraged the Drupalgeddon security vulnerability to let an intruder into Mossack Fonseca’s inner file store, which is likely on hosted on Oracle – an aging, business scale digital storage system. On a conventional Drupal site the ‘sessions’ database table hosts the strings which must be posted when a logged-in user visits a controlled access URL. After getting those strings the intruder could pose as any user by sending the same data as a regular user’s browser cookie would provide in a request.
If they were able to get administrative account credentials for the larger Oracle database whose existence Unicorn Riot can infer, then that could have facilitated remotely exfiltrating everything in this hypothetical, but probable, master file database.
Another avenue of attack: if PHP files can be directly executed by hitting the URLs, the intruder who can already pose as a system user (via session hijacking) could then upload a malicious PHP file which would be able to provide more database access credentials, or even a mechanism to fetch out files from the likely Oracle file server in bulk.
The portal isn’t the only vulnerability
Wired UK observed that another subdomain, owa.mossfon.com has an outdated Microsoft Outlook email platform, 2009 vintage, and added proof that the portal is vulnerable to the DROWN attack. The ACLU’s chief technologist Chris Soghoian observed that the email system lacks industry standard encryption protocols, which would have simplified intercepting any documents arriving or departing via email. [See Unicorn Riot’s interview with Soghoian about Analysts’ Notebook published Monday]
The BBC reports today that Mossack Fonseca considers itself the ‘victim of hack’. However, given the major problems with Mossack Fonseca’s well funded, yet poorly run digital infrastructure, one wonders how many billionaires’ lawyers are today contemplating suing Mossack Fonseca for gross negligence in their administrative duties?
With the huge news impact of this firm’s data leaks, peering deep into their flawed digital infrastructure helps demystify what they’re doing. It’s paper shuffling with familiar and badly maintained software, on an international scale that lets an unbelievable amount of cash be hidden away by elites around the world. Scrutinizing every detail of what they publish on the Internet can pay huge dividends, if you know where to look.